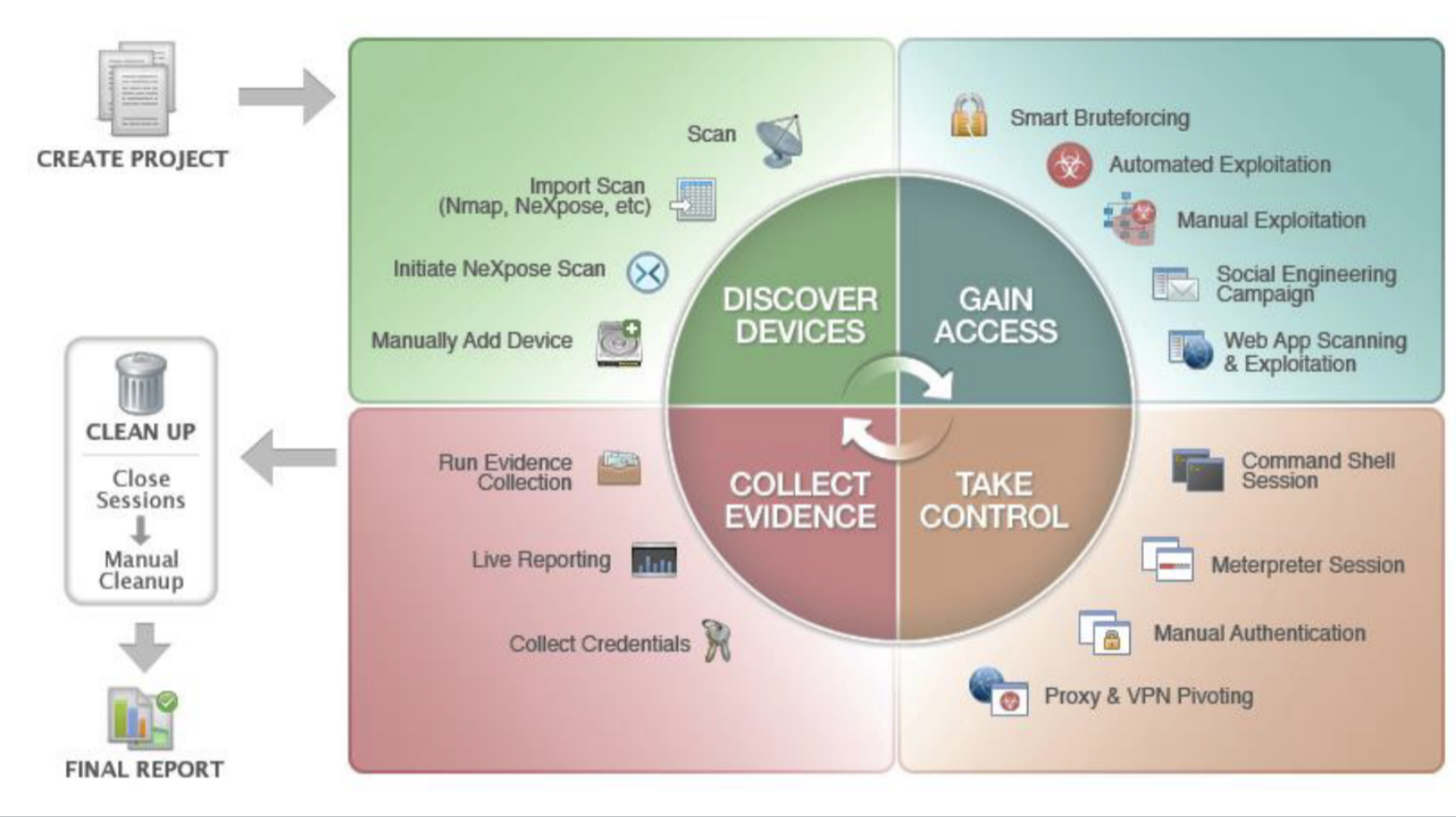
Generally, this helps researchers, developers, and security professionals to identify and address the vulnerabilities that would allow bad actors to attack or compromise the application or other IT resources. In practice, penetration testing involves performing several security tests or evaluations on servers, networks, websites, web apps, etc. While this may differ from one system and testing goal to the other, a typical process includes the following steps;
Listing of potential vulnerabilities and issues that attackers can exploit Prioritize or arrange the list of vulnerabilities to determine the criticality, impact, or severity of the potential attack. Perform penetration tests from within and outside your network or environment to determine if you can use the specific vulnerability to access a network, server, website, data, or another resource illegitimately. If you can access the system unauthorized, the resource is insecure and requires addressing the respective security vulnerability. After addressing the problem, perform another test, and repeat until there is no problem.
Penetration testing is not the same as vulnerability testing. While teams use vulnerability testing to identify potential security problems, penetration testing will find and exploit the flaws, hence establish if it is possible to attack a system. Ideally, the penetrating testing should detect the critical security flaws, hence provide an opportunity to fix them before the hackers find and exploit them. There are several commercial and free penetration testing tools that you can use to establish if your system is secure. To help you select the right solution, below is a list of the best free penetration testing tools.
Karkinos
Karkinos is a lightweight and efficient penetration testing tool that allows you to encode or decode characters, encrypt or decrypt files and text, and perform other security tests. Generally, the Karkinos is a bundle of multiple modules that, when combined, enable you to carry out a wide range of tests from a single tool. As such, some people refer to it as the ‘Swiss Army Knife’ for penetration testing.
Key features
Encode or decode characters in several standard formats, Crack hashes simultaneously using its built-in wordlist of over editable or replaceable 15 million breached or common passwords. Generate popular hashes such as SHA1, SHA256, SHA512, and MD5. Compatible with Linux and Windows. Interact and capture reverse shells, and more.
Sifter
Sifter is a powerful blend of various penetration testing tools. It comprises a combination of OSINT and intelligence gathering tools as well as vulnerability scanning modules. The Sifter combines multiple modules into one comprehensive penetration testing suite with the ability to quickly scan for vulnerabilities, perform recon tasks, enumerate local and remote hosts, check firewalls, and more.
Key features
Sifter consists of 35 different tools and the ability to scan websites, networks, and web applications. Uses Attack Surface Management (ASM) to map the attack surface. Has an exploitation tool to ethically exploit found vulnerabilities Advanced information-gathering capabilities The tool works on Ubuntu, Linux, Windows, Parrot, Kali Linux, and others. A large number of penetration testing modules hence highly scalable and customizable.
Metasploit
Metasploit is an advanced and versatile that helps testers to identify and exploit vulnerabilities. The tool enables you to prioritize while demonstrating the potential risks using a closed-loop vulnerability validation. Also, the feature-rich tool allows you to perform a wide range of testing that ranges from scanning and creating your payloads to performing exploits and test security awareness using simulated phishing emails.
Key features
It has an in-built discovery scanner for TCP port scanning on the target device. The scanning allows you to gain visibility of the services running on a network and identify open ports and vulnerabilities you can exploit. Vulnerability and configuration errors scanner to identify flaws and potential attack vectors Automated or manual exploitation of identified vulnerabilities. Allows you to access the target through password attack methods such as brute force or reusing credentials. Works on Windows, Mac OS, and Linux and available in both command line and GUI-based versions.
Sn1per
Sn1per is an all-in-one penetration testing tool for security teams and researchers. The continuous Attack Surface Management (ASM) platform lets you discover your application’s attack surface and vulnerabilities.
Key features
Allows you to discover your attack surface hence providing an opportunity to prioritize the real security threats. Automate the process of discovering the vulnerabilities as well as executing ethical exploits on identified flaws. Enables you to conduct a visual recon and scan web applications. – automatically collects basic recon (whois, ping, DNS, etc.). Manage vulnerabilities from a single location.
Commix
Commix is an open-source that helps to scan and exploit command injection vulnerabilities. The tool automates the flaw detection and exploitation processes hence increasing speed, coverage, and efficiency. Short for Command and injection and exploiter, Commix is an effective combination of a scanning tool and a command injection vulnerability exploiter.
Key features
Easy to use tool that automates the finding and exploiting of command injection flaws, hence makes it faster to identify and exploit vulnerabilities Exploits discovered command injection vulnerabilities It runs on Linux, Windows, and Mac standard operating systems and Kali Linux and other penetration testing platforms, such as Parrot security operating system. Portable, with the ability to test several operating systems and applications Modular design that allows you to add and customize functionalities to suit your requirements Allows you to perform either a result based command injection or blind command injection
BeEF
The Browser Exploitation Framework (BeEF) is a powerful and effective testing solution that concentrates on the web browser and its vulnerabilities. Unlike other tools, it uses the client-side attack vectors, which, in this case, are the vulnerabilities in web browsers, to access and assess the security posture of the target environment. The approach allows the testers to bypass the underlying perimeter security and then access and analyze the target’s internal environment. Key features
A modular structure with a powerful API and over 300 command modules that range from browser and router to exploits, XSS, and social engineering. Integrate with other tools such as Metasploit Ability to exploit identified vulnerabilities Network recon and ability to gather a wide range of information from hosts A GUI interface and support for Windows, MAC OS, and Linux It supports one or multiple browsers, hence allowing several testers to launch multiple test modules.
HackTools
HackTools is a powerful all-in-one web extension that includes various tools and cheats sheets for testing XSS payloads, reverse shells, and more. Generally, it is available as a tab or a pop-up option. Once you add the extension, you get a one-click feature that allows you to search for payloads in your local storage and on several websites.
Key features
It has a dynamic reverse shell generator. SQLi, XSS, Local file inclusion(LFI), and other payloads Provides you with several data exfiltration and download methods from remote machines Hash Generator for common hashes such as SHA1, SHA256, SHA512, MD5, SM3, etc. MSFVenom builder tool to quickly create payloads Works in conjunction with Metasploit to launch advanced exploits
Modlishka
Modlishka allows you to perform an automated HTTP reverse proxy. You can also use the tool to poison the HTTP 301 browser cache automatically. Further, you can use the tool to hijack non-TLS URLs. Usually, Modlishka supports most of the multi-factor authentication techniques and can identify and highlight 2FA vulnerabilities. Key features
It can strip a website from all security headers and encryption information. Ability to harvest user credentials Enables you to perform or simulate phishing campaigns to identify weaknesses and raise awareness about popular phishing techniques and solutions. Supports injection of pattern-based JavaScript payload.
Dirsearch
The Dirsearch is a command-line web path scanning tool. The feature-rich tool allows you to brute force webserver directories and files. Generally, it enables developers, security researchers, and admins to explore a wide range of general and complex web content with high accuracy. With a broad set of wordlist vectors, the penetration testing tool provides impressive performance and modern brute force techniques.
Key features
Detect, or find hidden and unhidden web directories, invalid web pages, etc Brute force webserver folders and files Multi-threading, hence improve scanning speed. Ability to save the output in different formats such as simple, CSV, markdown, JSON, XML, plain, etc Compatible with Linux, Mac, and Windows hence compatible with many systems.
sqlmap
The sqlmap is one of the best open-source tools for testing and finding SQL injection vulnerabilities in databases. The tools automate the finding and exploiting vulnerabilities that would result in SQL injection, database server takeover, etc. Also, it includes several switches such as over data fetching from the database, database fingerprinting, and using out-of-band connections to execute commands on the operating system, access the underlying file system, etc.
Key features
Provides a thorough scan of web applications while identifying SQL injection and database takeover vulnerabilities Detect and exploit vulnerable HTTP request URLs to access a remote database and perform actions such as extracting data like database names, tables, columns, and more. Automatically find and exploit the SQL vulnerabilities. For example, you can automate the process of detecting database vulnerabilities and eventually perform a database takeover. Supports several SQL injection techniques, including UNION query, stacked queries, error-based, Boolean-based blind, time-based blind, out-of-band, etc. Suitable for popular database servers, including Microsoft SQL Server, MySQL, PostgreSQL, Oracle, Firebird, IBM DB2, SQLite, etc It can recognize password hash formats automatically.
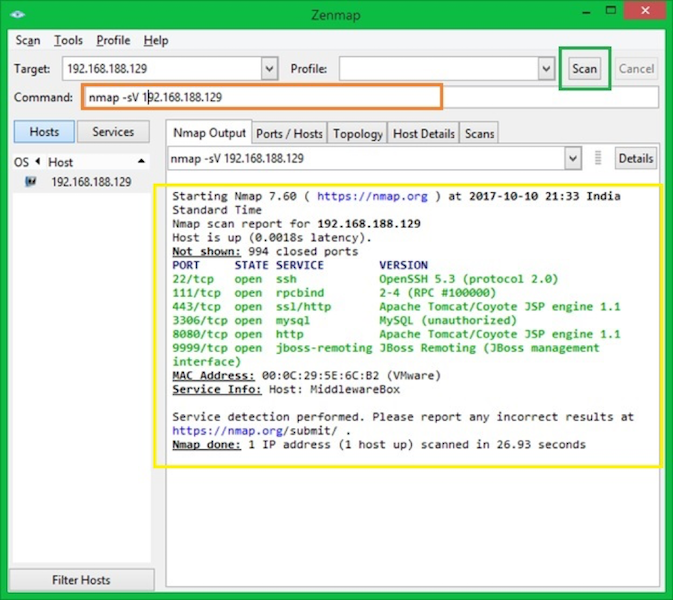
Nmap
Nmap is a security auditing and network discovery tool. The powerful, feature-rich open-source tool helps admins to perform network inventory, monitor service uptime, manage upgrade schedules, among many other tasks. The Nmap tool uses IP packets to find hosts on the network, operating systems, and active services. Other metrics the tool identifies include the firewalls or filters in use and others.
Key features
High flexibility solution that supports a wide range of techniques It uses TCP and UDP scanning mechanisms, version detection, operating system detection, ping swipes, and more. Powerful and scalable hence suitable for all networks, including large systems with thousands of machines. Easy to install and use the tool available in both command line and GUI version, and suitable for average and expert testers. Multiplatform support solution that works with most of the standard operating systems including, A scan-results comparison tool, packet generator, and response analysis tool.
Conclusion
Although it is almost impossible to make applications 100% secure, knowing the existing flaws enables the teams to establish if attackers can use them to break into the apps or systems. To perform the test, security professionals can use a wide range of open-source tools available in the market. Here is a quick SAST vs DAST comparison.